Effective communication is crucial for business success. Yet, ensuring confidentiality and security shouldn’t be ignored at any cost.
This guide explores 15 key elements that enhance the security of communication systems in business operations, grounded in industry research and expert insights.
But first, here’s the creamy layer of this guide along with a not-so-flashy graphic:
Key Takeaways
| Feature | Description | Benefits |
|---|---|---|
| End-to-End Encryption | Data is encrypted from sender to recipient. | Protects data from interception. |
| Multi-Factor Authentication | Requires multiple verification methods for access. | Enhances security against unauthorized access. |
| Access Control | Limits access to sensitive information. | Reduces risk of internal breaches. |
| Secure File Sharing | Encrypted platforms for document transfer. | Protects sensitive files during sharing. |
| Regular Software Updates | Keeps systems secure against vulnerabilities. | Ensures protection against the latest threats. |
Encryption Protocols
You’ve been using this one on a day-to-day basis already,
But where?
In your WhatsApp chats, and calls.
In simple words, encryption transforms data into a secure format, ensuring only authorized parties can access it.
No wonder, encryption is fundamental in safeguarding business communications.
Here are some types of encryption:
Types of Encryption
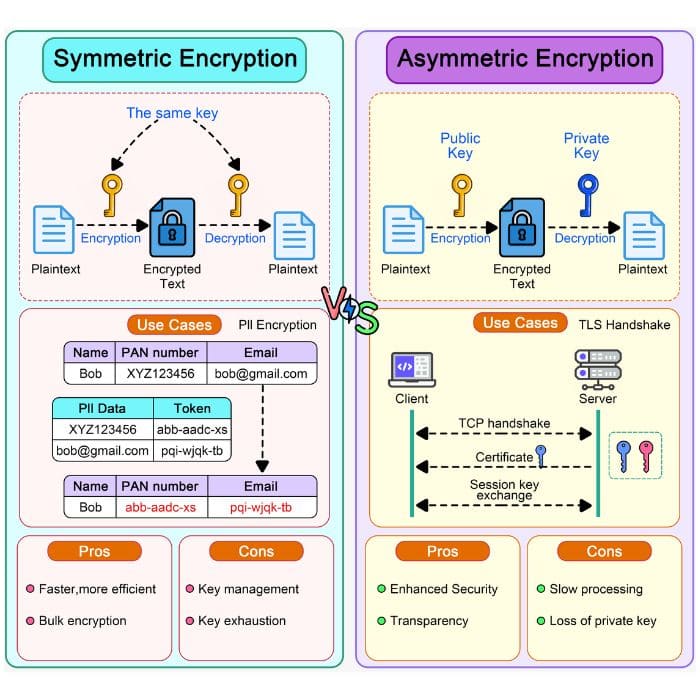
- Symmetric Encryption: Uses the same key for encryption and decryption. It’s efficient but poses key distribution challenges;
- Asymmetric Encryption: Uses a pair of keys—public for encryption and private for decryption. This method, though more computationally intensive, is crucial for secure key exchanges and digital signatures.
Here’s a visual breakdown for both the types:
Either of them will work just fine,
The deciding factor is to Implement robust encryption protocols like AES for data at rest and TLS for data in transit to maintain security and confidentiality within your organization.
Multi-Factor Authentication
QR code–based MFA setup and verification
During setup, present the user with a secure, one-time QR code (to scan with an authenticator app). For ongoing logins, optionally issue short‑lived, single‑use QR codes displayed within a secure session to validate user identity via a trusted mobile device.
To keep operations efficient and responsive, it often makes sense to hire the right number of experts for monitoring, incident escalation, and policy upkeep.
For businesses that handle a high volume of customer interactions, integrating security into a cloud based contact center solution can provide scalable, secure communication channels that align with regulatory requirements and industry standards.
To generate these secure codes reliably, you can use The QR Code Generator a trusted tool known for producing high-quality, customizable, and secure QR codes for business use.
Implementing Multi-factor authentication (MFA) adds an extra layer of protection, making it especially beneficial for businesses using payroll software for SMEs to ensure that sensitive payroll data is accessible only to authorized personnel.
Implementation Tips
- Combine something you know (password), something you have (token), and something you are;
- Use authentication apps and hardware tokens for robust security.
Secure Email Gateways
Unsecured business emails are like open backdoors inviting thieves with a warm hug. Secure email gateways protect against email-based threats like phishing and malware.

Here are some key features that will encourage you to start using secure email gateways.
Features
- Advanced threat protection;
- Data loss prevention;
- Encryption of emails in transit.
Regularly update and educate employees on email security practices to mitigate risks.
Virtual Private Networks (VPNs)
You might be quite familiar with this one but not as a possible solution to securing your business communications…
Virtual Private Networks or VPNs create secure, encrypted tunnels for data transmission, protecting against eavesdropping and interception of your data gold.
3 Easy Requirements for Choosing the Right VPN
- Ensure strong encryption standards (e.g., AES-256);
- Opt for a no-logs policy;
- Consider speed and server locations as per your needs.
Learn more about VPNs and privacy in our detailed VPN privacy guide.
Firewalls
Firewalls act as barriers between your network and potential threats, monitoring and controlling incoming and outgoing traffic.
We’re not talking about the normal ones found on your Windows 7 from the 2000s…
You must set up strong and dedicated firewalls to ensure the best protection.
Types of Firewall
- Hardware Firewalls: Physical devices that provide a strong layer of defense;
- Software Firewalls: Programs installed on individual devices;
- Cloud-based Firewalls: Ideal for businesses using cloud services.
Regular updates and configuration adjustments are essential for maintaining firewall effectiveness.
But first things first, go and set up a firewall right now if you don’t have one already.
Secure Messaging Apps
Secure messaging apps encrypt messages end-to-end, ensuring only the sender and receiver can read them.

Recommended Apps
- Signal: Known for its strong encryption protocols;
- WhatsApp: Popular for its user-friendly interface and encryption;
- Telegram: Offers secret chats with end-to-end encryption.
Adopt secure messaging apps for all sensitive communications within your organization.
In the ever-evolving landscape of digital security, secure messaging apps have become the unsung heroes of business communication, weaving an impenetrable tapestry of privacy around sensitive exchanges.
These digital fortresses not only shield your conversations from prying eyes but also serve as a testament to your organization’s commitment to data integrity.
By integrating secure messaging apps into your communication toolkit, you create a culture of vigilance that permeates every level of your enterprise, fostering trust among team members and clients alike.
As cyber threats grow more sophisticated, the adoption of these encrypted bastions becomes not just a security measure, but a competitive advantage, signaling to stakeholders that their confidential information is treated with the utmost respect and protected by cutting-edge cryptographic protocols.
Regular Security Audits
Conducting regular security audits helps identify and address vulnerabilities in your systems.
Steps in a Security Audit
- Define the scope and objectives;
- Identify potential threats and vulnerabilities;
- Assess existing security measures;
- Implement improvements based on findings.
Regular audits are crucial for maintaining a robust security posture and compliance with industry standards.
Endpoint Security
Endpoint security protects devices like laptops and smartphones from cyber threats.
Key Features
- Antivirus and anti-malware protection;
- Intrusion detection systems;
- Data encryption.
Implement strong endpoint security solutions to safeguard all devices within your network.
Data Loss Prevention (DLP) Systems
DLP systems monitor and protect sensitive data, preventing unauthorized access or leaks (IBM – United States).
Components of DLP
- Content discovery;
- Monitoring and protection of data;
- Enforcement of security policies.
Integrate DLP solutions to monitor data at rest, in use, and transit.
Secure File Transfer Protocols (SFTP)
SFTP ensures secure file transfers, protecting data from interception and unauthorized access.
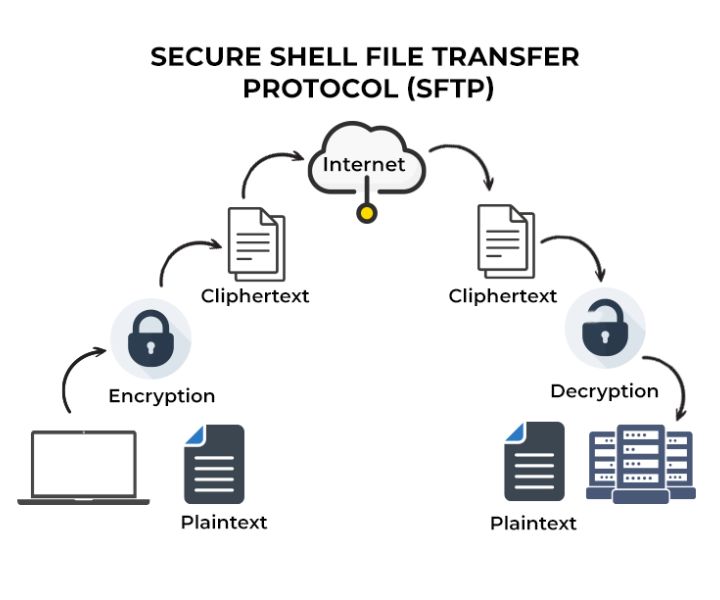
Benefits
- Encryption of data during transfer;
- Protection against data breaches;
- Secure authentication.
Choose SFTP over traditional FTP for enhanced security in file transfers.
Secure Socket Layer (SSL) Certificates
SSL certificates encrypt data transmitted between a website and its users, ensuring secure communications.
Types
- Domain-validated (DV): Basic level of security;
- Organization-validated (OV): A higher level of validation;
- Extended Validation (EV): The highest level of trust.
Implement SSL certificates for all web services to protect sensitive data.
Intrusion Detection Systems (IDS)
IDS monitors network traffic for suspicious activity, alerting administrators to potential threats.
IDS Types
- Network-based IDS (NIDS): Monitors entire networks;
- Host-based IDS (HIDS): Focuses on individual devices.
Regularly update and configure IDS to detect and respond to new threats.
Employee Training Programs
Employees are often the weakest link in security. Regular training ensures they are aware of potential threats and how to avoid them.
Participating in online courses can further enhance their understanding and skills, keeping them updated on the latest cybersecurity practices and protocols.
To enhance productivity and improve time management within your team or workflow, it is highly recommended to utilize productivity tools such as project time tracker software or task management software.
Key Training Topics
- Phishing awareness;
- Password management;
- Safe internet practices.
Measure the effectiveness of training programs and update them regularly.
Access Controls and Permissions
Access controls ensure that only authorized users can access sensitive information.
Best Practices
- Use the principle of least privilege;
- Regularly review access rights;
- Implement strong authentication methods.
Effective access control management is crucial for maintaining data security.
Incident Response Plan
An incident response plan outlines steps to take in the event of a security breach.
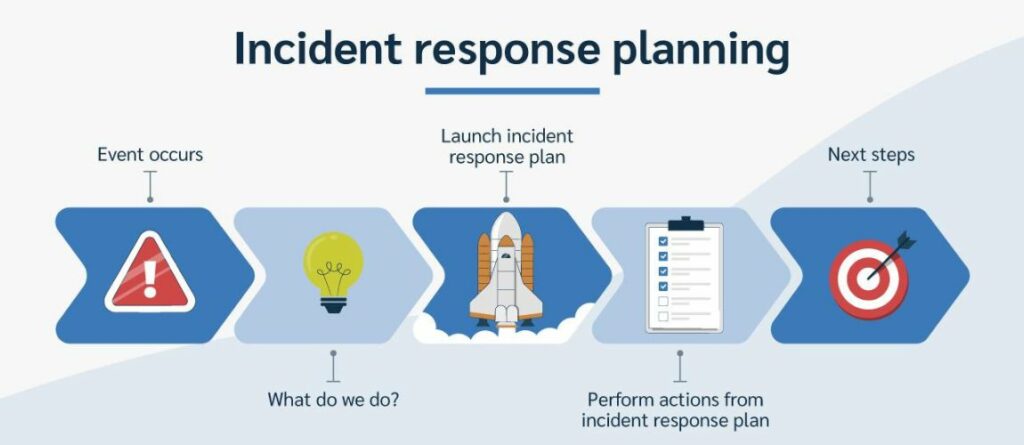
Key Components
- Preparation and identification of potential incidents;
- Containment, eradication, and recovery steps;
- Regular testing and updates.
Having a robust incident response plan minimizes damage and ensures a swift recovery.
How Can Businesses Enhance Customer Confidence Through Secure Communication?
Building customer confidence is crucial for any business. Successful entrepreneurs starting a business recognize that implementing robust security measures early establishes long-term client trust and brand credibility.
When clients know their data is secure, they are more likely to engage and convert.
But what are the initial steps to leverage this approach?
Here are some strategies:
- Transparent Policies: Communicate your data protection policies to clients;
- Informed Consent: Allow clients to understand the risks and benefits before sharing data;
- Regular Updates: Keep clients informed about security measures and updates.
Consent Management Solutions play a vital role here by streamlining how businesses obtain, store, and manage consent for data collection and processing. These solutions ensure compliance with global privacy laws, making it easier for businesses to protect customer data and maintain trust.
In today’s skeptical market, mere promises of data protection fall flat – consumers demand visible evidence of security through trust signals like recognized certification badges and real-time protection indicators during transactions. Smart businesses now recognize that security isn’t just a technical requirement but a powerful marketing advantage that deserves prominent placement in customer communications.
The most successful companies have learned to transform potentially anxiety-inducing security discussions into confidence-building moments that actually strengthen customer relationships rather than creating friction in the sales process.
What Are the Emerging Trends in Secure Communication?
The way how secure communication works is evolving at a rapid pace (all thanks to the AI hype and growing security concerns).
Here are some trends for eyeballing:
- AI-Powered Security: Artificial intelligence is being used to detect and respond to threats in real-time;
- Zero Trust Security Models: This approach assumes that threats could be both outside and inside the network. It requires strict verification for every user;
- Decentralized Communication Platforms: These platforms reduce reliance on central servers, enhancing security.
The Bottom Line
Incorporating the key elements we discussed, into your business operations can level up your communication systems’ security. Thus, it will protect your valuable data and maintain the trust of your clients and partners. As technology evolves, staying informed and adaptable to new security measures will be critical in safeguarding your business operations against new cyber threats.