Is Your Session Hijacked? How to Prevent Session Hijacking?
Every time you log in or access a website or server on the network you initiate what is called a “session”. Sessions represent a connection between the user’s computer or other device and a server and are what makes the exchange of information and data between two computers on the network possible.
Most websites use cookies. These are temporary files in your web browser that allow the website to remember that you are logged in and authenticated. However, just like real-life cookies, someone can snatch them away from you.
This is called session hijacking, or cookie-side jacking. This is different from TCP session hijacking as HTTP is an application-level protocol, whereas TCP is a network-level protocol.
What is Session Hijacking and How Does it Work?
A session hijacking attack comes in different forms (more on that later), but in general, it takes advantage of poor session management to steal away cookies. With these cookies, a hacker can then fool the server into believing that they are an authenticated user.
This means that a hacker can do pretty much anything that an authorized user could and can:
- Access the real user’s personal information (identity theft);
- Encrypt valuable user’s data and demand ransom;
- Steal money from the user’s bank account;
- Buy stuff from the web store;
- And more.
What are the Main Session Hijacking Methods?
Session hijacking attack can take different forms depending on the attacker’s position or attack vector. We can first differentiate between two major types of session hijacking:
- Active
In active session hijacking, the hacker kicks your own device out of the session and completely takes over the session.
- Passive
In passive session hijacking, the real user is still logged into a session, while the hacker is spying on the traffic and collecting sensitive information such as your passwords.
Now let’s look at the main session hijacking methods hackers use:
- Cross-site scripting (XSS)
Cross-site scripting or just XSS is a code-injection attack in which the attacker takes advantage of a website or application vulnerability to inject a malicious code into the user’s computer. Once the user accesses the site, they activate the script and the attacker can hijack their cookies.
Websites and applications that are based on JavaScript (JS) are particularly vulnerable to XSS. Unfortunately, JS is required for encryption services and many otherwise legitimate services will use JS to inject code into your device.
CTemplar protects its users from harmful JS injection by using checksums, which allows users to compare the code in their browser with the code in Github in just 15 to 30 seconds (this would normally take valuable hours or even days without checksums).
- Session fixation
Another method a hacker can use to steal the user’s cookie is to provide a session key they already know. This can be done in a few ways;
- The hacker can send a login form with a hidden fixed session ID for the user to fill out;
- They can send an email link with an HTTP query parameter so when the user clicks on the link, using the session key provided by the attacker, the latter can hijack their session;
- Also, the hacker can manipulate the HTTP header values and insert a known session key with the Set-Cookie parameter (this method requires that the attacker also has access to the user’s network traffic).
- Session-side jacking
Session-side jacking employs packet sniffers which allow the hacker to monitor user’s traffic and intercept session cookies as they (user) authenticate themselves on the server. For websites that only use TLS/SSL encryption for login (but not the rest of the session), an attacker can “allow” the user to login and then, using the sniffer, hijack an already logged in session and impersonate the user.
- Using malware to hijack cookies
One way for hackers to steal session cookies is to install a malicious software or malware on the user’s device. This is usually done using an email link that leads the user to a malicious website. Once the malware is installed on the user’s machine, the malware will automatically scan their network for session cookies and send them to the attacker.
How to Prevent Session Hijacking?
Session hijacking, aka cookie-side jacking/hijacking takes advantage of the vulnerabilities in the HTTP protocol. HTTP is stateless, which means it requires session cookies to allow a website or application to identify the user’s device and store their current session.
As you can see, this poses several security risks.
So what can be done to prevent session hijacking?
First, here are some methods on the user or client side:
- Don’t click or open unknown links in your email.
These links can contain malware or lead the user to an infected website and are often used in email phishing.
- Don’t use public WiFi.
Avoid using public WiFi hotspots like cafes, public parks, airports and similar when you have to log in to your bank account as they typically have poor security and can be hacked easily.
- Stay away from unsecured websites.
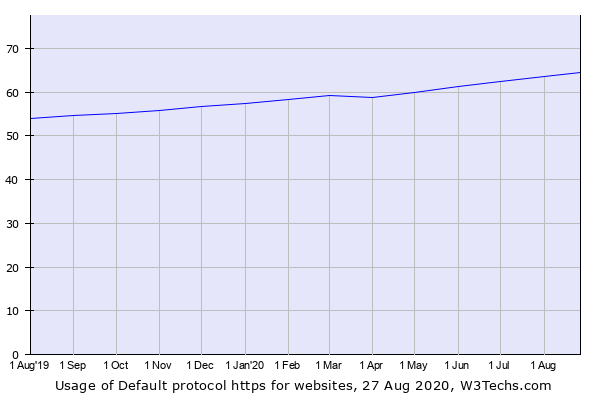
Today more than 60% of all websites on the web use HTTPS according to W3Techs Usage statistics of Default protocol https for websites analysis. Just to be clear, an HTTP website isn’t inherently bad, however, it is far less secure than an HTTPS one.
- Install anti-malware.
Hackers will inevitably try to install malware on your computer and most times you won’t be aware of it, especially if you don’t have an anti-malware program to protect your computer.
We can also look at some methods to prevent session hijacking on the server-side, or by websites themselves:
- Use HTTPS instead of HTTP.
This will allow your website to use TLS/SSL encryption on all your pages and sessions and not just for login and thus stop session-side jacking.
- Use web frameworks.
Don’t try to invent hot water or, in this case, your own session management. Instead, use web frameworks, which provide tested and secure session ID generation and management.
- Regenerate session keys.
After a successful user authentication at login, regenerate the session key right away to avoid session fixation.
- Set the http0nly attribute.
To prevent JavaScript injection and Cross-site scripting, set the Http0nly attribute using the Set-Cookie HTTP header. This will block access to cookies from the client-side.
Worried about the safety of your email data? Sign up today to CTemplar armored email. CTemplar provides state-of-the-art security for all your email data and provides full anonymity for its users.