Understanding the Fileless Malware Attacks Surge and how to Protect Against Them
Cyber-criminals and other threat actors will seek (and often find) ways to install malicious files on your computer. However, there is a type of malware attack that doesn’t need to do that.
The fileless malware attack.
What fileless malware does instead is hide in your system and piggyback on otherwise legitimate processes and programs running in your computer to execute malicious attacks.
Since fileless attacks are not file-based, but memory-based, it makes it much harder for antivirus programs to detect them as they don’t leave a “footprint” like regular malware attacks.
What is a Fileless Malware?
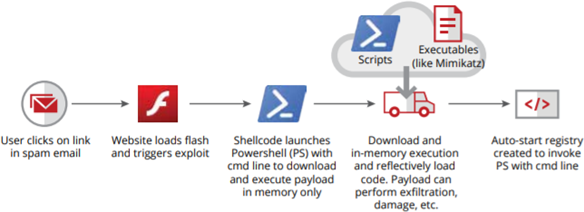
A fileless attack can be extremely challenging for AV software to detect as we already said. This is because it doesn’t leave any footprints or rely on files.
Instead, fileless malware will use a legitimate program to infect your computer.
This is a relatively new type of malicious software, since it first appeared in 2017 as a mainstream type of attack. In recent years, however, it has been gaining in popularity more and more among cyber attackers.
For example, according to this Internet Security Report by WatchGuard, the fourth quarter of 2020 saw a fileless malware attacks surge of almost 900% compared to the same period in 2019.
Chief technology officer at WatchGuard, Corey Nachreiner commented:
“The rise in sophisticated, evasive threat tactics last quarter and throughout 2020 showcases how vital it is to implement layered, end-to-end security protections. The attacks are coming on all fronts, as cyber criminals increasingly leverage fileless malware, crypto minters, encrypted attacks and more, and target users both at remote locations as well as corporate assets behind the traditional network perimeter. Effective security today means prioritising endpoint detection and response, network defences and foundational precautions such as security awareness training and strict patch management.”
How does a Fileless Malware Attack Work?
Normally, malware requires that the user clicks on a malicious link or downloads a file in order to install itself. This is usually done through a malicious file sent to the user via a phishing email or freeware software that the user downloads and that contains hidden malware.
Fileless malware, however, doesn’t need an entry point like that, making it easier for malware to evade detection by anti-virus software.
That being said, there are a few scenarios in which a fileless malware will most commonly appear:
- Injecting malicious code on applications such as JavaScript or Word that are already installed on your computer. The applications themselves will remain operational while they’re hijacked by the malware;
- Clicking on malicious links or downloading malicious files in a phishing email. These then load on your computer and allow hackers to execute malicious attacks remotely;
- Using Microsoft PowerShell to infiltrate multiple machines. This is called “lateral infiltration”;
- Through fraudulent websites. These particularly target Flash plugins to run malicious code in the user’s browser memory;
- Via native applications such as Windows Management Instrumentation (WMI). This can make the fileless malware particularly difficult for the network security to catch on as it latches on to such programs remotely.
Using Endpoint Detection and Response (EDR) Solutions to Defend Against Fileless Malware
As legacy antivirus solutions prove quite ineffective when dealing with fileless malware attacks these require a different approach based on endpoint detection and response (EDR) solutions.
Both the user and the system play an important role in defending against malicious behavior and fileless attacks, so effective security needs to include both.
Endpoint detection and response solutions monitor incoming and outgoing network traffic in real-time, as well as PowerShell and WMI applications to prevent cyber criminals from easily injecting malicious code and breaching the system and network defences of its victim.
In addition, keeping software up to date, especially Microsoft applications and monitoring any regular activity from PowerShell are equally as important in defending against threat actors like this.
Finally, some best practices against fileless malware attacks include:
- Making sure that your software is up to date;
- Double-checking on applications and programs before installing them;
- Keeping an eye out on phishing emails and not clicking on links or downloading files that could contain malicious code in them.
Conclusion
Fileless malware attacks have been growing in popularity and over the last few years we have seen these kinds of attacks surge.
These attacks are not easy to detect with traditional network security, but instead may need a more advanced endpoint protection. Most importantly, however, is to keep an eye on the user behavior and avoid making things easier for hackers.
Hopefully, these tips will help your system and network to remain operational in the wake of rising encrypted malware rates and network attacks.
FAQ
A fileless malware attack is a type of malware that uses a legitimate program to infect the victim’s computer. This type of malicious software attack is memory-based, instead of file-based, making it difficult to detect by regular antivirus software and therefore requires more advanced endpoint protection.
The single biggest ransomware attack in history was the WannaCry ransomware attack. This attack occurred in May 2017 and infected 7000 computers in just one hour.