What Ransomware Negotiation Really Looks Like?
Every year, ransomware attacks cost businesses over $133,000 on average. In addition to this, businesses also lose $8,500/hour as a result of the downtime that the ransomware causes.
But should you be paying off threat actors what they ask to get your stolen data back or can you reduce ransomware payments to a more “acceptable” level?
It all depends on how good you are at ransomware negotiation so we’ll take a deep look into the whole process and see how you can get back your sensitive data for less than what the ransom demands.
What is a Ransomware Attack?
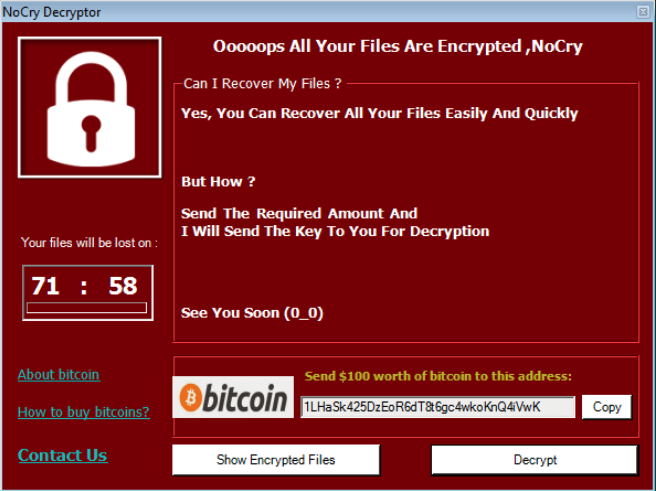
In 2019, over 200,000 businesses lost access to their sensitive data due to a ransomware attack.
Few have managed to fully recover.
What exactly is ransomware?
Ransomware is a kind of malicious software that can allow the cyber attacker to lock and encrypt the victim’s computer or system unless they agree to their ransom demand.
Once the business has paid the ransom, the ransomware gang promises to decrypt data and release its confidential data.
How to Negotiate a Lower Ransom Payment?

Most businesses (60% from 300 that participated in the Nester International Security Council survey) said they’d be willing to pay ransomware attackers if their organization is compromised.
The first question is really, should you pay the ransomware or not?
Federal agencies and law enforcement, for instance, recommend that companies avoid paying ransomware gangs, saying that this only leads to further attacks.
According to the Senior Data Analyst at Gartner, Mark Harris:
Deciding whether to pay ransom is a difficult decision and one that must be made carefully at the board level, not by security and risk leaders. Understanding what happens if you pay is key to making that decision.”
So should you be paying ransom or not?
To answer this, you need to know what cybercriminals have stolen in the first place.
Have they stolen any sensitive data, such as customer data or personally identifiable information?
If that’s the case you might still have to pay the ransomware group, but knowing what exactly was stolen can put you in a better position at the ransomware negotiation table to pay less, or even nothing at all.
Do You Have to Pay What Threat Actors Demand and the Role of a Ransomware Negotiator

Here’s the thing, even if you agree to pay the ransom to get your stolen data back, you often don’t have to pay exactly what ransomware groups demand when they first contact your company.
Thankfully, you don’t have to go through the ransomware negotiation process on your own. In fact, it’s a good idea to hire the services or professional ransomware negotiators instead.
The whole process (ransomware negotiation that is) happens very quickly and starts when attackers send out a ransom note to the victim and they respond. Once they’ve done that, it usually takes 10 to 15 exchanges on IM or via chat conversations to “reach an agreement”.
Or, as a threat intelligence analyst at GuidePoint Security, Drew Schmitt says:
“Once you reach out and engage the threat actor, that’s going to be kind of when your proverbial clock starts. That’s when they know that you’re aware of the situation, you’ve reached out to them, and they’re going to kind of have this timeline in their head of how long this negotiation process should take.”
Keep in mind, however, that the ultimate decision of whether to make a ransomware payment and how much to pay is not up to the ransomware negotiator, but you and your company.
What ransomware negotiators can only do is give you an extra helping hand and counsel based on their previous dealings with that ransomware group.
Ransomware Groups Don’t Have a Lot of Patience

Ransomware groups happen to be very busy, and as they’re hitting your company, they are probably doing the same to another three or four.
They’re running a business here so they want the ransomware negotiation to be as quick as possible. This means they might lose patience if they think you’re stalling or they get annoyed with you.
They instead want to keep the process as linear as possible. For instance, if the company takes too long to respond, or they’re specific in their counteroffers, the threat actors might decide to stop the negotiations and publish the data without giving away the decryption keys.
Should You Hire a Ransomware Negotiator or Can You Do it Yourself?
Do you need to hire a ransomware negotiator?
Perhaps not, but unless you know negotiation tactics well, the decision not to hire one might seriously backfire.
In fact, for Micheal Philips, co-owner of the cyber insurance company Ransomware Task Force, hiring a negotiator is a “no-brainer”.
There are two main reasons for that:
- They are better at negotiating these kinds of things than you are;
- They might already be familiar with the ransomware group and how they operate.
Ransomware negotiators know well what the actual price on the dark web is for something like personally identifiable information depending on the company size and what ransom amount based on that should the company really pay.
Additionally, if they’ve dealt with the ransomware gang before, negotiators can also know how flexible they might be in negotiations and how much they’d be willing to lower their ransom demands in the first place.
Prevention is the Best Form of Protection Against Ransomware Attacks
Ultimately, however, the best way to protect your organization and sensitive data against ransomware is to prevent it.
This means:
- Keep your software and operating system up to date;
- Install anti-virus and anti-malware software;
- Only download programs from known and authorized sources;
- Don’t click on suspicious links or download email attachments;
- Avoid disclosing your PII to unknown email senders and falling prey to phishing emails;
- Keep backups of all your important data and files for easier data recovery;
- Create a recovery process in case your company becomes a victim of a ransomware attack.
However, with ransomware incidents growing in popularity over the last few years (350% up in 2018), prevention might not always be enough and you might need the ransomware negotiation services of a professional company like GroupSense.